
I recently attended Embedded World conference in Nuremberg, Germany, alongside our partners MULTOS. It was a busy 3-day event, with all the main players there from MCU Suppliers, Distributors, Technology vendors and Service suppliers.
Security was a hot topic at the show, all the main MCU vendors were promoting a Secure by Design approach throughout, focusing on key provisioning and key insertion for initial device trust and device provisioning. They are offering this either through the MCU manufacturer’s own factories (for large customers) or through their distribution network channels. Distributors are setting up services for key provisioning and onboarding as driven by these chip/IC manufacturers.
In Device Authority terms, we call this step 1 and 2 in our Enterprise IoT security blueprint; provisioning root keys and certificates at time of manufacturing (secure production) and secure device onboarding.
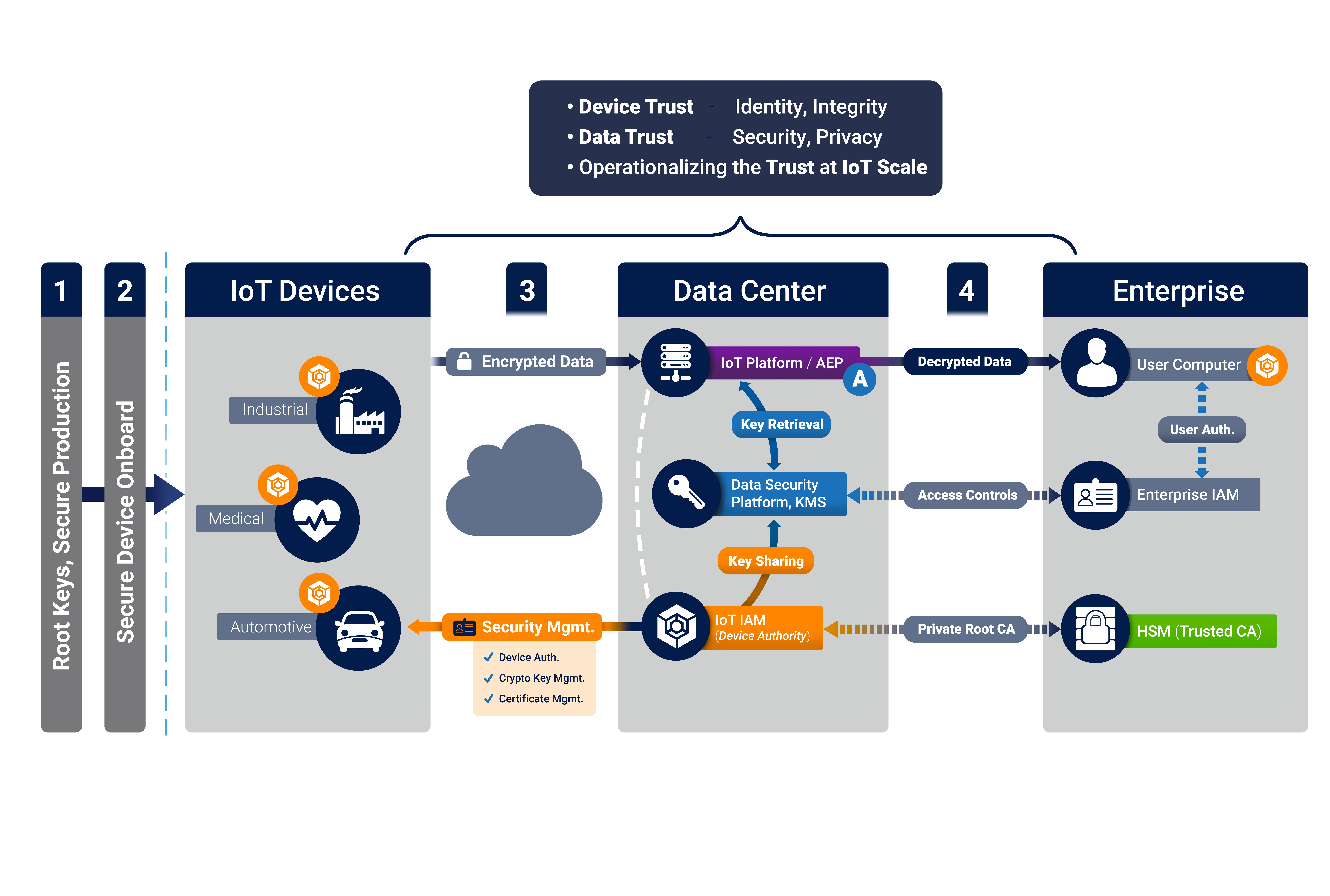
However, the MCU manufacturers are still yet to realize and figure out steps 3 and 4. These become particularly important when you get into the real detail of use cases. Every use case is different with a vast range of requirements.
Just think about all the different IoT Platforms that are out there, PTC ThingWorx, Microsoft Azure IoT Hub, AWS IoT, Google Cloud (to name a few). Then consider how to integrate with the enterprise and enterprise security operations such as HSMs or third party CAs. This goes far beyond the initial key insertion and device onboarding.
Let’s see how this evolves over the coming months, exciting times ahead.
Download our Enterprise IoT Security Blueprint to learn more.
