
Back in October 2016 we experienced the Mirai botnet malware, which had its fair share of press coverage after taking down popular websites and services including Twitter, Airbnb and Netflix. Mirai leveraged the use of weak credentials, particularly passwords – usually guessing the default passwords which manufacturer’s ship devices with. The solution? Easy, just update your password!
Ask yourself a simple question – If you bought a new home from a builder or a previous owner, would you use the same alarm code or passcode key for the house alarm system, and never bother to change it. Of course not, but some do. Think through the potential sequences. But this is not enough.
More recently we were introduced to Persirai, a more advanced version of Mirai discovered by Trend Micro. Likely to have evolved due to the Mirai code being made public, Persirai has more aggressive features by exploiting a zero-day vulnerability to steal the password file from a an IP camera regardless of password strength. We now find ourselves in a situation where simply updating your default password is no longer enough.
To prevent your IoT devices being targeted in a DDoS attack by the Persirai botnet, organizations need to deploy strong security that focuses on the current password problem – not only changing them regularly, but also ensuring they are encrypted. Improved security practises must be adopted, and lessons learned from enterprise security management must be applied.
KeyScaler provides superior protection from Persirai through its automated password management solution, which:
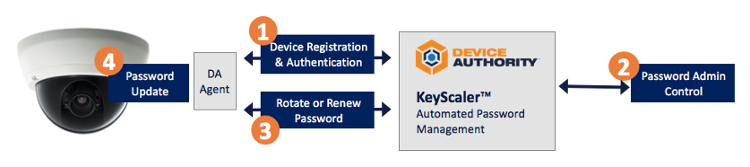
Watch a quick video demonstrating Automated Password Management to Axis Cameras.
