
$6 trillion will be invested in the Internet of Things (IoT) between 2015 and 2020, which will yield $12.6 trillion ROI over the next decade.
Until now, security has been treated as an afterthought; by adding layers of security after devices are delivered, and infrastructure and applications are already in place. Security for the IoT is too important to be treated an afterthought. To realize the full potential, the IoT ecosystem is forcing security from the beginning, built as part of the device and infrastructure.
In this series of blogs, we will look at the key security issues and how to address them.
The IoT is a new interconnection of technology heralded as the next industrial revolution – implying radical change, disruption, and an entirely new paradigm for the planet. Specifically, the IoT is an extension of the existing connections between people and computers to include digitally-connected “things.”
One of the things that makes the IoT so disruptive is that its impact isn’t restricted to a single sector or function. From consumer devices to jet engines, logistics to product development, healthcare to municipal planning, enterprise IoT is having a huge impact. It’s helping farmers tackle climate change issues and dramatically increase yields. It’s helping cities meet the challenges of rapid urbanization and making life better for citizens in the process. And it’s enabling utilities companies to modernize ageing infrastructure while increasing efficiency and monitoring costs.
The compelling economic and social benefits envisioned with this disruptive IoT ecosystem (Digital and Physical) is at risk as we do not have a way to manage the scale and complexity of the device centric relationships and data.
IoT brings new security challenges introduced by the scale and pace of adoption, as well as the physical consequences of compromised security. We have already read stories about companies being hacked, identities stolen, and even app-connected cars being hijacked. Often, default device settings equate to “wide open” and even when access controls are present, many organizations do not have strong security protocols in place. This is the IoT equivalent of having a username/password combo of “admin” and “password”, which was the case in the last major attack.
Existing security solutions evolved as an afterthought for the changing digital world. We now have an opportunity to include security in the design stage, in the new IoT world.
An IoT security breach goes beyond simple data loss, it’s also a safety issue, with potentially disastrous impact. We need to ensure IoT security is built in from the start to realize its full potential. The IoT has many economic impacts and value creation capabilities across many industries and for the consumer. Everyone, including Governments, regulatory bodies and standards groups are being forced to rethink this issue.
IoT security will be complicated by the fact that many ‘things’ use simple processors and operating systems that may not support sophisticated security approaches.
Disruptive Change – Identity:
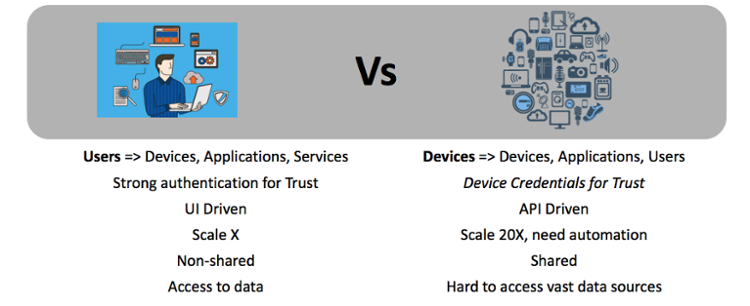
The key theme of this blog is “Trust the Device, Trust the data” as the IoT device is the weakest link in the chain.
Securing the perimeter with IoT begins and ends with the device.
Before we go into the details on implementation approaches, let’s look at the key areas that require immediate attention:
Register/Enroll the devices into IoT IAM platform and Applications
Provision owner controlled security
IoT Authentication
“Things” (Device) Integrity
Data Privacy, Integrity
Secure Upgrades
Please stay tuned for the next blog in this series, including detailed design recommendations for many of the problems/challenges listed above, and more.
If you want to hear more, please register for our next webinar with MultiTech and NextGenID; “IoT IAM – What’s it all about?”
