
Code signing is a software development process of digitally signing executable code to prove the identity of the software author AND guarantees that the code has not altered or corrupted since it was published. Both these points are extremely important for building trust from your customers and safely distributing your software.
As the number of Internet of Things devices and applications continues to grow in 2020, unauthorized software and firmware updates are a major threat vector for IoT cyber-attacks. IoT breaches can have physical consequences that result in loss can also introduce substantial legal liability and erode brand reputation and trust, with immense costs due to certificate recall, breach response, as well as loss of overall revenue.
In short, your software is your product and your product is your brand. If cybercriminals or a rogue employee push out a malicious software update to your customers, they will blame you for failure to protect them rather than the individuals responsible for the malicious update.
With attacks becoming increasingly sophisticated and hard to defend against, they can cost organisations a lot of money each year. According to an Accenture report, the average cost of cybercrime grew by more than $1 million in 2018 to $13 million (about £9.9 million) per organisation. Due to the implications of these costs, people are extremely cautious when it comes to downloading executable files from the internet. It’s worth doing whatever it takes to gain their trust. Online distribution means you can distribute software updates faster. This broadens your potential customer base and there can be considerably savings since there is no software media, packaging or postage costs.
Enterprise organizations need a method to trust and verify IoT device updates as these unverified devices are easy entry point for attackers. Any unsigned updates can be tampered in transit, so there is a need to prevent malicious updates being applied to devices.
However, code signing software may no longer be enough to prevent cybercriminals from their work as they now target the theft or misuse of private code signing keys. They use these to either code sign malware or tamper with your software. It’s been reported that over 22M code signing keys have been stolen or forged from legitimate businesses. This should be a concern to ALL software-oriented businesses.
To protect against theft and misuse, companies need to implement a secure code signing process to protect their private code signing keys. Enforcing cryptographic and other certificate policies, limiting access to code signing keys, requiring approvals for each use of private code signing keys, and never allowing a code signing key to leave secured storage, even for a code signing operation, are a few steps that should be taken.
But these crucial security steps can interfere with the develop/build/release/deliver software process, especially in situations where a code signing system isn’t integrated with the development teams’ tools and if it can’t be automated. What’s the result? Development teams bypass security measures, or try to handle it on their own, often incorrectly. This is especially true for IoT.
Today there is a severe lack of integration with existing enterprise systems. Existing code-signing solutions are not integrated with the enterprise IoT workflows and existing IoT code-delivery processes not readily integrated with code-signing workflows. As new IoT Project are created, new solutions are built from scratch for each use-case, which inevitably means expensive bespoke development work.
To address the challenges for an effective code signing solution, especially for IoT Enterprise projects, we (Device Authority) have teamed up and integrated with Venafi’s CodeSign Protect solution for the Code signing part and Microsoft (Blob Storage) for the software delivery part, with our KeyScaler platform playing the role of conductor to orchestrate the process.
KeyScaler provides an automated solution to manage the lifecycle of updates that are delivered to a device. Provisioning unique certificates, establishing trust between a device and server, signing code using a pre-configured Certificate Authority with policy-based authorization, and delivering encrypted assets to IoT devices – without requiring any human intervention.
This solution closes the gaps open to exploitation by integrating and using Venafi CodeSign Protect to secure the code signing process throughout the secure update lifecycle.

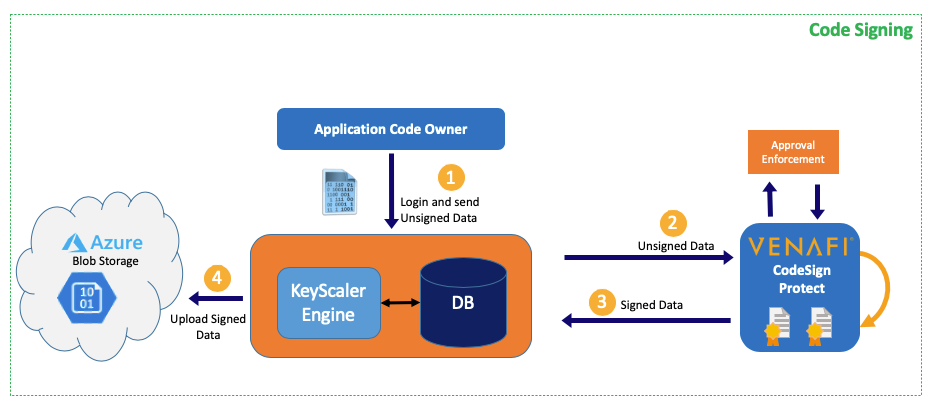
This can be accomplished in 3 simple steps:
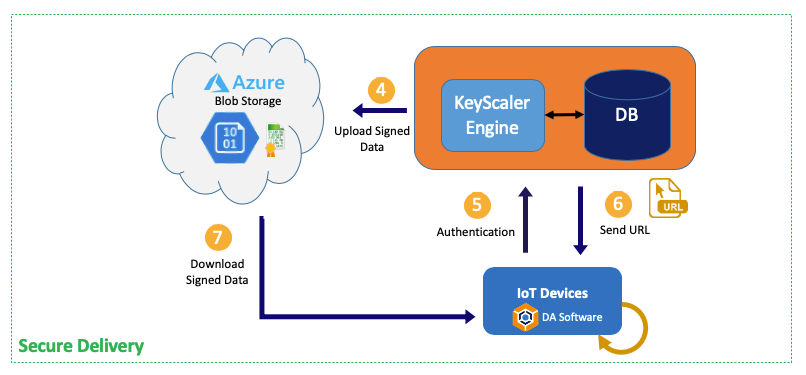
Through seamless integration between Venafi CodeSign Protect and Device Authority KeyScaler the solution allows you to secure your code signing and update delivery process for IoT devices and deliver critical requirements for IoT environments:
Blog by Nirmal Misra, Device Authority and Eddie Glenn, Venafi.
