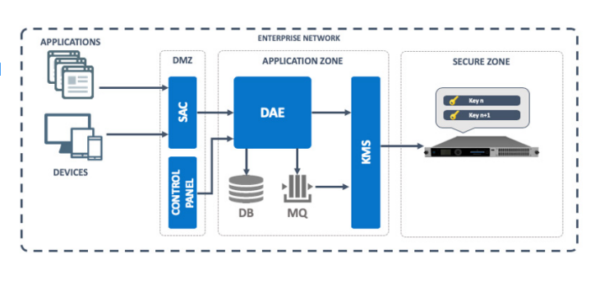
What is the HSM Access Controller (HAC)?
The HSM Access Controller (HAC) delivers granular authentication, authorisation and audit controls for IoT devices, servers, and applications. Enterprise applications and services connecting to HSMs will authenticate to KeyScaler and use KeyScaler REST APIs to consume common HSM operations, such as key generation, data signing, data crypto, and general public key storage.
What are the benefits of HAC?
- Prevents unauthorized access to critical HSM infrastructure
- Mitigates security risks and liability exposure
- Implements granular access policies for HSM to support key use cases
- Provides an audit trail for compliance
- Protects brand reputation
- Cost savings (operational and financial) derived from avoiding security breaches
- Eliminates custom development, accelerate time to market
- IoT Ready – Only solution to support headless and constrained devices