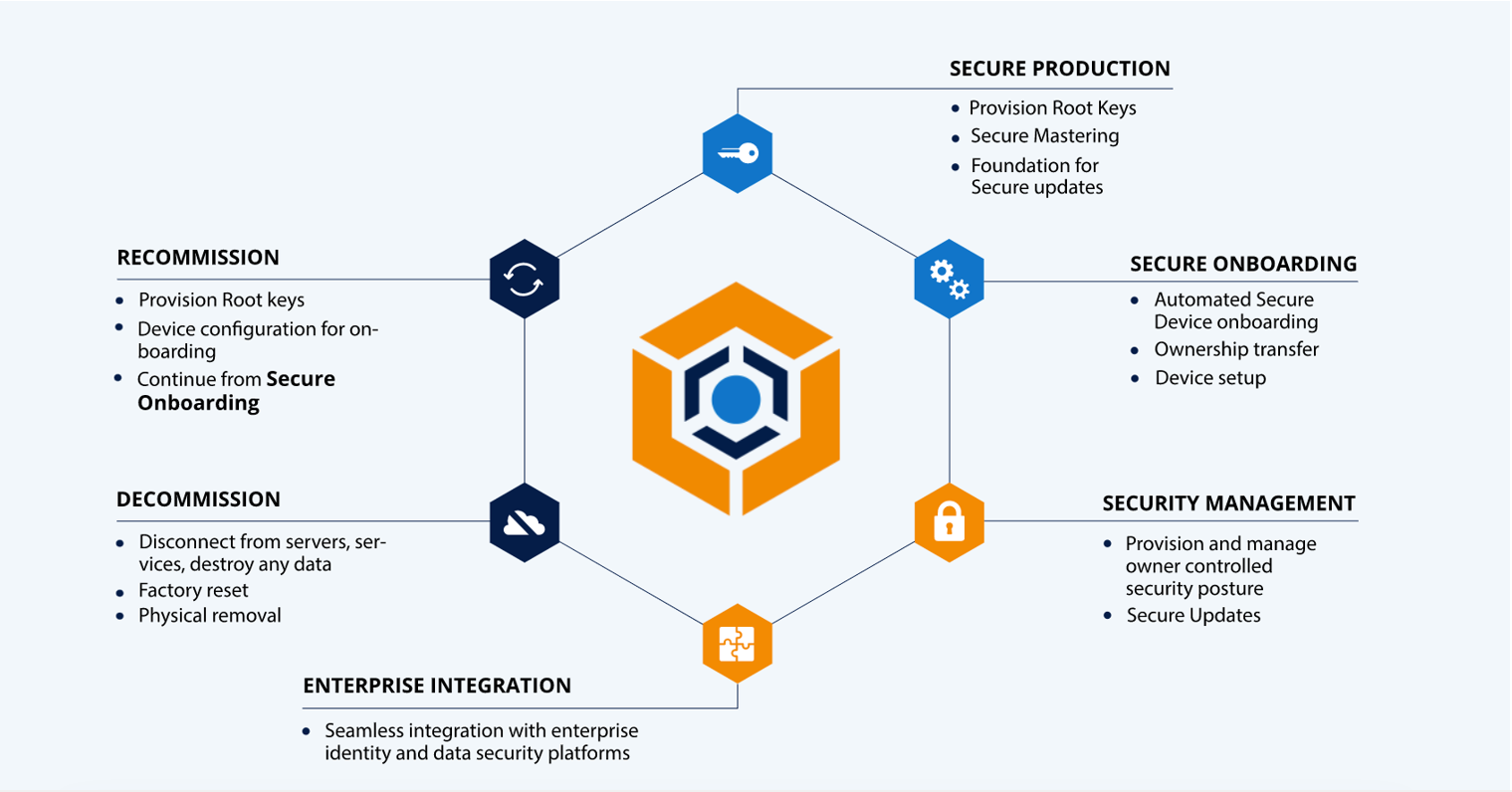
Without automation, managing the full lifecycle of connected infrastructure such as IoT devices, or OT devices on your factory floor, opens your organization to significant cyber risk. Tedious manual processes lead to human error, slow responses to cyber-attacks, and introduce the potential for supply chain disruptions. KeyScaler® establishes device and data trust across your supply chain through fully automated Device Identity Lifecycle Management, removing the risk of human error, significantly improving response and recovery times from attacks, and increasing your ROI for critical assets.
KeyScaler® uses patented technology that supports authentication of brownfield devices with inadequate security for today’s cyber threat landscape, and supports authentication of secure-by-design devices using credentials established during the manufacturing process.
KeyScaler is designed to easily integrate with your existing enterprise security infrastructure including PKI platforms, Hardware Security Modules, and cloud applications. Our platform comes equipped with pre-built integrations to a rich ecosystem of security partners that are available as simple configuration options during the onboarding process.
KeyScaler® provides frictionless security for connected devices, enabling total device, data and operational trust. But the return on using KeyScaler is more than just security…
Use our calculator to see how automating your device authentication can not only ensure device security but also offer a return on investment.
By telling us how many connected devices you have in operation now as well as how many you plan to have in the future, we are able to compare your investment in KeyScaler with the average cost of manually provisioning devices and rotating certificates.
